JS Business Solutions Blog
Today’s businesses need an established cybersecurity strategy. It’s as simple as that.
However, many businesses need guidance to create this strategy, which is why the National Institute of Standards and Technology has developed a framework for proper cybersecurity protection. Let’s walk through this framework and discuss what you need to do to meet its requirements.
The concept of a four-day-long workweek is one of the latest trends that businesses of all shapes and sizes are pondering. It has been touted to have significant benefits for both their operations and the employees who carry them out. However, is the “compressed” workweek the route your business should go?
Well, as is so often the answer, that depends. Let’s examine the concept of a compressed workweek and its application more closely.
By now, you know that every business needs to prioritize its entire security footprint, including technology. The security technology used in businesses today has a huge effect on the overall security of an organization. This means that you have to have a coordinated effort that allows your security initiatives to consider your business’ IT. In today’s blog, we’ll show you how effective organizations consolidate their security using IT.
Today’s businesses have to deal with many risk factors, especially cybersecurity and its many related concerns. At this year’s Cybsafe Impact 2024 USA conference, intended to share human risk management insights, a very accomplished panel of experts shared various thoughts.
Let’s explore some of the topics this panel spoke on.
In today's digital landscape, data breaches and privacy concerns are more prevalent than ever. Your team needs to protect important information by following data privacy practices, which also helps boost your company's reputation. It needs to be a part of your company culture.
Here are effective strategies to encourage a culture of data security within your team.
The idea of a four-day workweek—where the common 40-hour week is shortened to 32 with no reduction of benefits or take-home pay—is becoming increasingly popular, boasting improved efficiency and heightened levels of employee satisfaction.
Naturally, as an IT provider, we’re intrigued by the idea of using technology to get the most out of this abbreviated time in the office.
Your business will not remain the same throughout its lifecycle, and as such, you need the services you utilize to be capable of changing with it. This is where it helps to have the flexibility and scalability of a managed IT provider on your side. Let’s go over why flexible technology is the path forward for SMBs like yourself and how you can take full advantage of the range of services an MSP can offer.
When it comes to network security, there are many common suggestions from IT professionals, like utilizing robust firewalls and antivirus measures. However, it’s easy to overlook some of these practices, especially if you are not necessarily a trained IT technician. We’re here to provide a short guide to three of the most common security pitfalls organizations like yours will likely face during normal everyday operations.
What’s the difference between a power strip and a surge protector? It turns out, quite a lot, and the difference is much more than just the number of plugs on it. Let’s discuss some of the biggest ways that these two important pieces of power supply technology differ and how you should determine which one best suits your needs.
Of all the aspects that play a part in your business’ success, its company culture can often be overlooked as nothing more than a perk… something nice to offer the team, but ultimately unimportant. This is very much a misconception.
Let’s discuss how valuable a positive company culture is, and how to develop one in your business. Don’t worry, we’ll get into the technology of it all, too.
Against all odds, remote work has been gradually accepted, but regardless of how your organization does it, it would be imprudent to overlook the obvious cybersecurity risks presented by remote work. Let’s take a look at the essence of zero-trust security and explore why it has evolved into the standard that organizations of all sizes should adhere to.
It’s hard to believe that it’s already been a few years since circumstances… “encouraged”... so many businesses to suddenly adopt work from home policies. As these circumstances have gradually normalized, many businesses have elected to keep these policies in place, either maintaining fully remote operations or shifting to hybrid operations.
However, some notable businesses have taken efforts to roll back remote work capabilities, if not discontinuing them entirely.
“If a craftsman wants to do good work, he must first sharpen his tools.” Like so many of the other quotes attributed to Confucious, this phrase is no less true today, even in the realm of business technology. It should come as no surprise that implementing the right technology for your particular business needs will produce greater results.
The real question is how to identify the technology that will contribute to the overall success of your organization.
How much technology does your business use day in and day out? More likely than not, it’s a lot, and we’d bet good money on the fact that you could be doing more to manage it. That said, it’s not always clear how to go about doing it, especially if you don’t have any in-house IT talent to handle this considerable responsibility. With managed services, you can overcome this challenge. Let’s go over what these are and how they work.
Cybersecurity is a complicated beast. Not only do you have to be sure that you’re protected from threats coming from outside your business, there are also a few very real threats that can originate from inside your business, too. Both are critical to prevent, which can be quite effectively accomplished via a zero trust approach to your security.
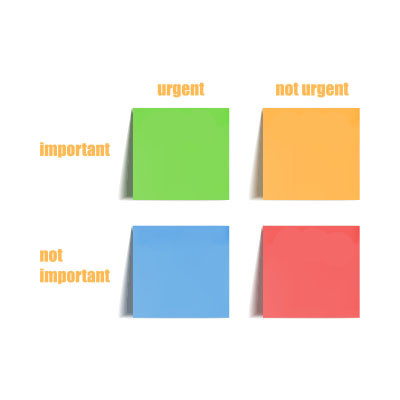
The modern worker has a lot of challenges and one of them is a laundry list of tasks to accomplish. For this reason, it’s best to have a plan for tackling your to-do list. One of the most effective ways to prioritize tasks is through what is called the Eisenhower Matrix. Inspired by a speech given by the former President of the United States and the Supreme Commander of the Allied Expeditionary Force in World War II, the Eisenhower Matrix simplifies complex task lists to make getting through them more effective. Let’s take a look at how it works.